Security Tools and Best Practices for Administrators
In addition to Cisco Meraki's secure out of band architecture and hardened datacenters, Cisco Meraki offers a number of tools for administrators to maximize the security of their network deployments. Use of these tools provide optimal protection, visibility, and control over your Cisco Meraki network. This page contains information about how to quickly and easily increase the security of your meraki.cisco.com accounts and our recommended best practices for account control and auditing.
Enable two-factor authentication
Two-factor authentication adds an extra layer of security to an organization's network by requiring access to an administrator's phone, in addition to her username and password, in order to log in to Cisco Meraki's cloud services. Cisco Meraki's two factor authentication implementation uses secure, convenient, and cost effective SMS technology: after entering their username and password, an administrator is sent an a one-time passcode via SMS, which they must enter before authentication is complete. In the event that a hacker guesses or learns an administrator's password, she still will not be able to access the organization's account, as the hacker does not have the administrator's phone. Cisco Meraki includes two-factor authentication for all enterprise users at no additional cost.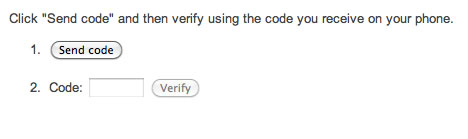
Strengthen your password policies
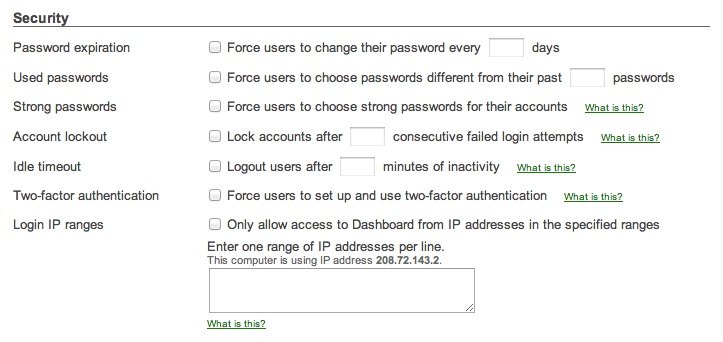
You can configure organization-wide security policies for your Cisco Meraki accounts to better protect access to the Cisco Meraki dashboard. Under Organization -> Configure, you may:- Force periodic password change (e.g., every 90 days)
- Require minimum password length and complexity
- Lock users out after repeated failed login attempts
- Disallow password reuse
- Restrict logins by IP address
Enforce the principle of least privilege with role-based administration
Role-based administration lets you appoint administrators for specific subsets of your organization, and specify whether they have read-only access to reports and troubleshooting tools, administer managed guest access via Cisco Meraki's Lobby Ambassador, or can make configuration changes to the network. Role-based administration reduces the chance of accidental or malicious misconfiguration, and restricts errors to isolated parts of the network.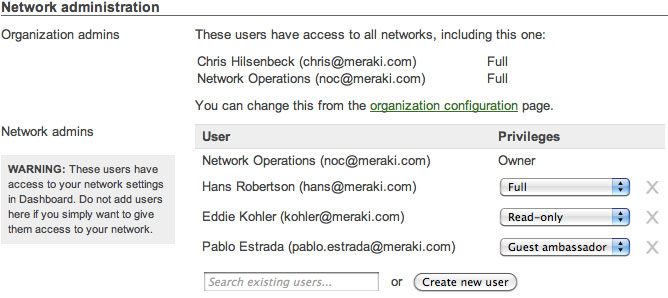
Enable configuration change email alerts
The Cisco Meraki system can automatically send human-readable email alerts when network configuration changes are made, enabling the entire IT organization to stay abreast of new policies. Change alerts are particularly important with large or distributed IT organizations.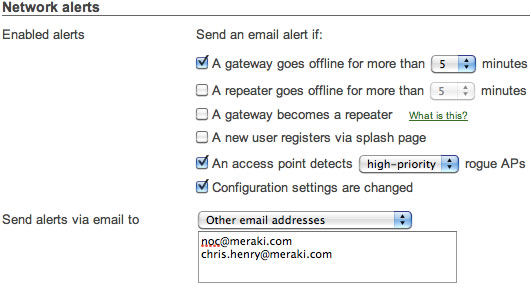
Periodically audit configuration and logins
Cisco Meraki logs the time, IP, and approximate location (city, state) of logged in administrators. Additionally, Cisco Meraki provides a searchable configuration change log, which indicates what configuration changes were made, who they were made by, and which part of the organization the change occurred in. Auditing configuration and login information provides greated visibility into your network.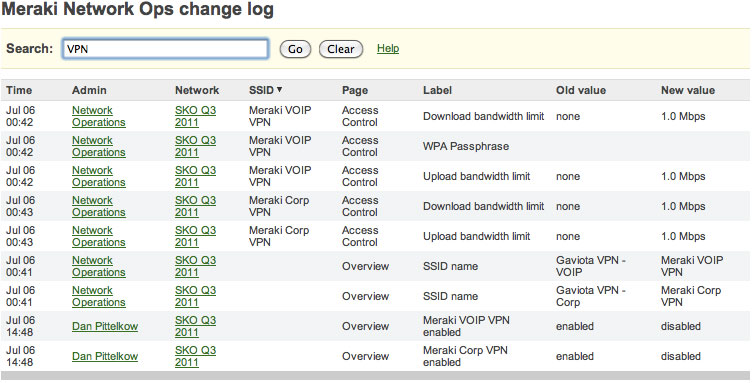
Verify SSL certificates
Cisco Meraki accounts can only be accessed via https, ensuring that all communication between an administrator's browser and Cisco Meraki's cloud services is encrypted. As with any secure web service, do not log in if your browser displays certificate warnings, as it may indicate a man-in-the-middle attack.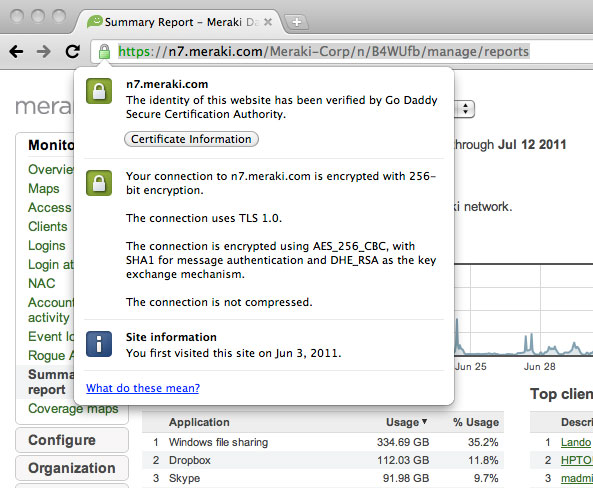
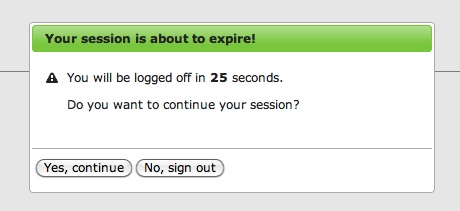
Idle Timeout
30 seconds before being logged out, users are shown a notice that allows them to extend their session. Once time expires, users are asked to log in again.